Enhancing Application Security with OAuth 2.0 and OpenID Connect
Enhancing Application Security with OAuth 2.0 and OpenID Connect
Introduction
In the era of interconnected systems and data sharing, ensuring the secure and seamless flow of information is crucial. Two prominent protocols that have revolutionized the authentication and authorization landscape are OAuth 2.0 and OpenID Connect (OIDC). These open standards provide secure ways for applications to access user data without sharing their credentials.
OAuth 2.0: A Revolution in Authorization
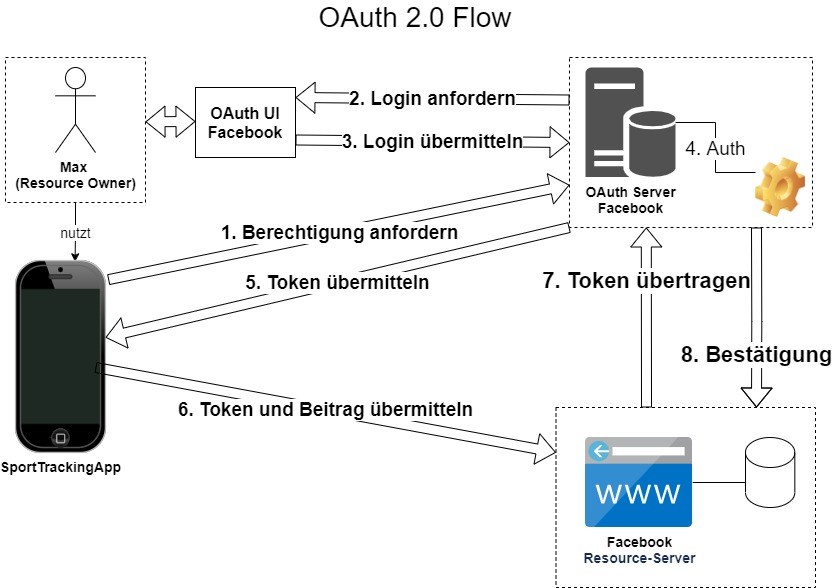
OAuth 2.0 is an open standard for access delegation, enabling third-party applications to obtain limited access to user data on another service, without exposing the user's credentials. For example, an app might need to access a user's Google or Facebook data, and OAuth 2.0 offers a secure way to do this.
Here's a typical OAuth 2.0 flow:
The user initiates the OAuth 2.0 process by clicking a button or link, such as "Sign in with Google."
The application redirects the user to the service provider's website, where the user logs in and authorizes the app to access their data.
The service provider redirects the user back to the application, including an authorization code in the URL.
The application retrieves the authorization code and requests an access token from the service provider.
The service provider returns the access token, which the application can use to access the user's data.
OAuth 2.0 offers multiple authorization grant types to accommodate different application types and scenarios. These include the Authorization Code Grant, Implicit Grant, Resource Owner Password Credentials Grant, Client Credentials Grant, and Refresh Token.
OpenID Connect: Extending OAuth 2.0 for Authentication

While OAuth 2.0 focuses on authorization, it doesn't provide a way to obtain information about the user's identity. This is where OpenID Connect (OIDC) comes into the picture. OIDC is an identity layer built on top of OAuth 2.0. It introduces an id_token, a JSON Web Token (JWT) that contains information about the user's identity, which the application can decode and use.
The OIDC flow is similar to OAuth 2.0, but the service provider returns an additional id_token when the application requests an access token:
As with OAuth 2.0, the user initiates the OIDC process by clicking a button or link.
The application redirects the user to the OIDC provider's website, where the user logs in and authorizes the application.
The OIDC provider redirects the user back to the application, including an authorization code in the URL.
The application uses this authorization code to request an access token and an id_token from the OIDC provider.
The OIDC provider returns the access token and id_token. The application can use the access token to access the user's data and decode the id_token to obtain the user's identity information.
Why Use OAuth 2.0 and OpenID Connect?
OAuth 2.0 and OIDC come with significant advantages:
Enhanced Security: They eliminate the need for users to share their credentials with third-party applications, reducing the risk of credentials being stolen or misused.
Improved User Experience: With single sign-on (SSO), users only have to authenticate once to access multiple applications, which simplifies the user experience.
Scalable User Management: As the user information is managed by the OAuth/OIDC provider, applications can offload user management tasks, making it easier to scale.
Interoperability: Being open standards, OAuth 2.0 and OIDC ensure interoperability across different systems, making it easier for developers to integrate with various services.
In conclusion, OAuth 2.0 and OpenID Connect play an essential role in enhancing the security and user experience of modern applications. By understanding and implementing these protocols, developers can provide users with a seamless and secure online experience.